Mobile Blockchain, Scalability Issues and Potential Future.
Hashing algorithms, Immutable ledgers, Distributed P2P networks
So far in history we have had many methods to prove the validity of time sensitive documents. Documents such as contracts, IPs, land ownership records, etc. Older popular methods include:
But In almost every case the only way to disprove or validate the claims is to inspect for tampering. This relies heavily on human expertise and like with everything humans do there is a scope for errors.
A block is essentially a way of storing time-sensitive information in a way that can be easily checked and verified with computers instead of humans. A blockchain is simply put a collection of many such blocks.
This gets extremely important essentially in this day and age with more documents choosing a digital form where they can easily tampered with. What is needed is a method of time-stamping digital documents with the following two properties.
Enter the hashing algorithm, its a cryptographic function which can convert any arbitrary length string into bit-strings of a fixed length. For example, the sha256 hashing algorithm used by the bitcoin network can convert literally anything into a 64 character, 256 bit hexadecimal string.
for any x, x_1 ; h(x) = h(x_1) is never possible. There are no duplicates.
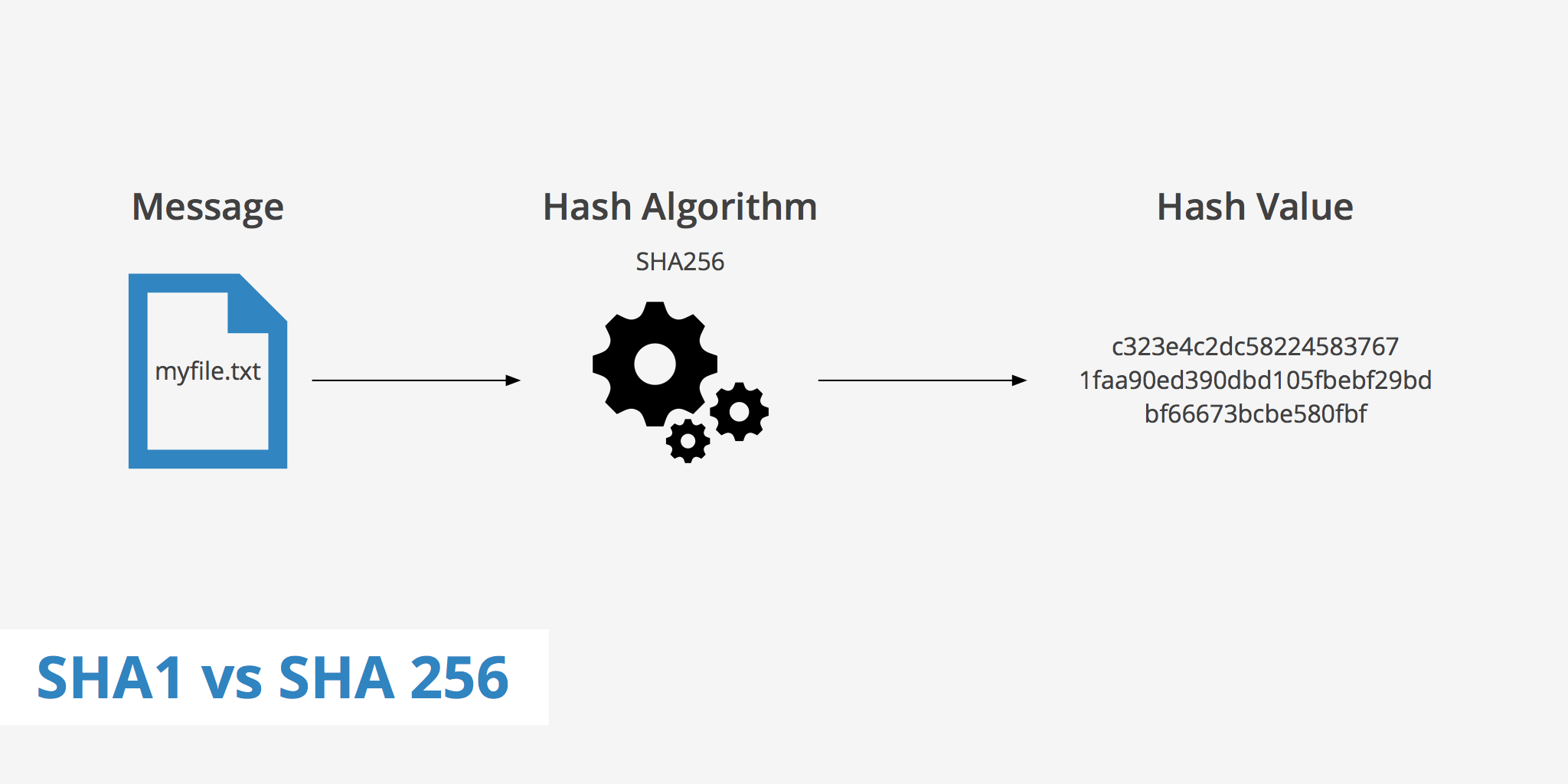
Any small change even a single bit will then change the hash value completely. This is called the avalanche effect.
To learn more about Hashing functions click here To learn more about the time-stamping of documents click here You can try a demo of hashing here
The blockchain is officially a digital, decentralised, distributed ledger. You might wonder how this next-generation technology is at its core a boring book. But being an immutable ledger is the core principle/property of the blockchain.
Any information that has to be stored has to be immutable ie, cannot be changed any further. This is done to ensure that no entry will ever be tampered with.
A simple blockchain achieves this in a simple way, let me explain.
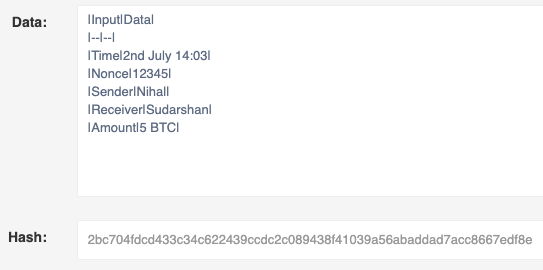
| Input | Data |
|---|---|
| previous block hash | “xyz” |
| Time | 2nd July 14:03 |
| Nonce | 12345 |
| Sender | Nihal |
| Receiver | Sudarshan |
| Amount | 5 BTC |
Say this is an example block containing the transaction information of me sending 5 BTC to my friends. I have mentioned the time of the transaction and a number called the nonce(will get to later). We know take this information and pass it through the SHA-256 and mine it. Mining is essentially calculating the nonce for the data where the hash can be within a limit(will be explained in detail later in the article).
Now we move to the next block and create some more hashes. Since we link each block with the hash of the previous block. Even a minor change in the information of any block will lead to the change in every single hash in the entire chain. In the event this sort of change occurs the chain is rendered corrupt and the previous proper version is restored.
You can try a demo version here
“Decentralization” is one of the fundamental and is commonly used in privacy focused projects. Although it is the at the core of its application the definition and meaning is very poorly defined. Here I have made my attempt to portray the intuition behind the concept instead.
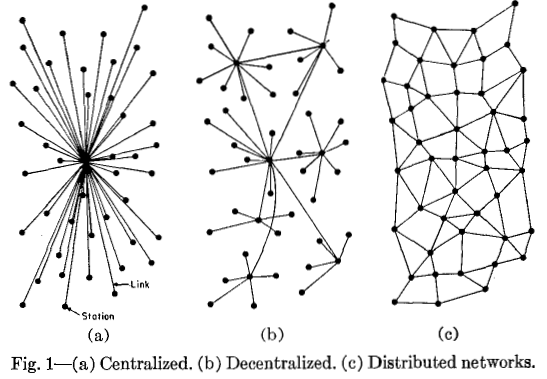
Traditional systems, be it computer servers or banking systems all use the centralized network. All the computation, responsibility and ownership is heavily almost completely controlled by the central entity. “distributed means not all the processing of the transactions is done in the same place”, whereas “decentralized means that not one single entity has control over all the processing”. Meanwhile, the top answer on the Ethereum stack exchange gives a very similar diagram, but with the words “decentralized” and “distributed” switched places! Clearly, a clarification is in order.
So here’s my take on it -
The next question is, why is decentralization useful in the first place? There are generally several arguments raised:
